On the SmallBusiness.com WIKI, we’ve shared the benefits of two-step verification on your email and financial-related accounts. We’ve also provided how-to information about two-step verification approaches for several of the most-used web services. In other posts, we’ve described an approached called “social engineering” that cyber-criminals use to convince people to share information with them that can be used in their efforts to access an account. Now, attackers are using social engineering to trick people (including you and your employees) into providing them with information related to your two-step password verification process.
In their recently released 2016 Internet Security Threat Report, Symantec describes many ways cyber-criminals are becoming more sophisticated in their efforts to crack the accounts of businesses, large and small, including new approaches to convince individuals to provide them with information that can help them get around a two-step verification password. For example, the illustration below describes a social engineering scam that attackers are using in their attempts to access Gmail accounts.
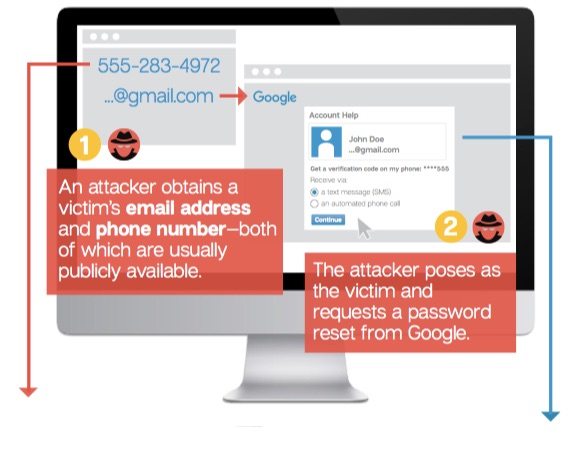

Advice on computer and network security from Symantec’s Internet Security Threat Report
As attackers evolve, there are many steps businesses and consumers can take to protect themselves. As a starting point, Symantec recommends the following best practices. (Be sure to share these with your employees.)
For Businesses
Don’t get caught flat-footed | Use advanced threat and adversary intelligence solutions to help you find indicators of compromise and respond faster to incidents.
Employ a strong security posture | Implement multi-layered endpoint security, network security, encryption, strong authentication and reputation-based technologies. Partner with a managed security service provider to extend your IT team.
Prepare for the worst | Incident management ensures your security framework is optimized, measurable and repeatable, and that lessons learned improve your security posture. Consider adding a retainer with a third-party expert to help manage crises.
Provide ongoing education and training | Establish simulation-based training for all employees as well guidelines and procedures for protecting sensitive data on personal and corporate devices. Regularly assess internal investigation teams—and run practice drills—to ensure you have the skills necessary to effectively combat cyber threats.
For Consumers
Use strong passwords | Use strong and unique passwords for your accounts. Change your passwords every three months and never reuse your passwords. Additionally, consider using a password manager to further protect your information.
Think before you click | Opening the wrong attachment can introduce malware to your system. Never view, open or copy email attachments unless you are expecting the email and trust the sender.
Protect yourself | An ounce of protection is worth a pound of cure. Use an internet security solution that includes antivirus, firewalls, browser protection and proven protection from online threats.
Be wary of scareware tactics | Versions of software that claim to be free, cracked or pirated can expose you to malware. Social engineering and ransomware attacks will attempt to trick you into thinking your computer is infected and get you to buy useless software or pay money directly to have it removed.
Safeguard your personal data | The information you share online puts you at risk for social engineered attacks. Limit the amount of personal information you share on social networks and online, including login information, birth dates and pet names.
